By Dominic Chorafakis, P.Eng, CISSP – March 20, 2019
Email continues to be the favorite tool for hackers to hijack computers and steal information. Recent phishing campaigns are proving to be particularly effective by combining different techniques to target Office 365 users. There are two key elements that make the attack effective:
- Malicious messages appear to arrive from known contacts
- Messages contain PDF attachments which do not carry any malware so they get past anti-virus. The goal is to entice users to click on a link that appears to take them to OneDrive or Office 365
Taking the time to verify the email address that a message appears to be from is an important step in security awareness. Some times the domain portion of the email address (the part that comes after the @ sign) will be a clue that the sender isn’t really who they claim to be. Unfortunately, it is not enough to just look at the From field, the sender’s email account may have been hacked, but also sophisticated hackers are able to spoof the From field to make it look like an email was sent by someone else.
It is important to note that this is not personal or specifically targeted, so don’t assume you are safe just because hackers don’t know who you are. Once a computer becomes infected, the malware will automatically extract information from contact lists and earlier email messages and automatically launch a similar attack against those contacts. It doesn’t even need to be someone you know who was infected. Say your friend Bob sends you an email inviting you to a party, and copies you and 10 other people you don’t know. If any one of those 10 people are infected, the malware will try to send an email from Bob to your email address with the malicious PDF without ever knowing you or Bob personally.
The malicious email may contain a link in the message itself, but in this case, we are focusing on the attack specifically targeting Office 365 users. In those attacks, when you open the PDF file, it will try to get to click on what looks like a legitimate link, here’s an example

If a user is tricked into clicking on the link, what happens next depends on the specific type of attack.
In some cases, the user is directed to a website that looks like a real Office 365 login page as seen below.
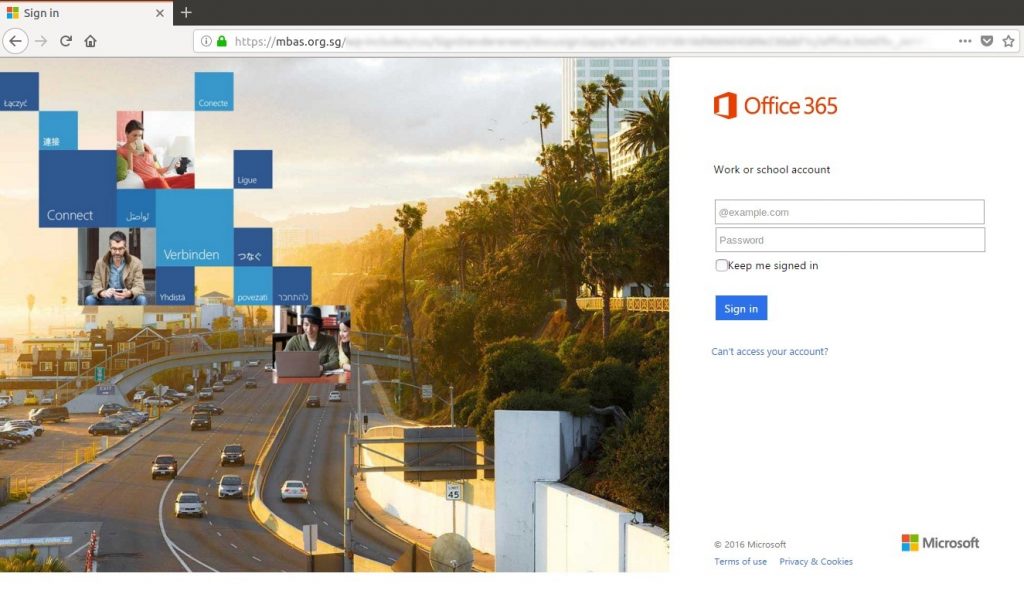
Note the URL in the browser is not Microsoft’s at all.
In this case the attacker is trying to trick the user into providing their username and password which will be sent to the hacker instead of Microsoft.
In other cases, clicking on the link will take to you a website that hosts software known as an Exploit Kit that will attack your PC looking for a vulnerability that can be used to install malware on it.
What to do
- Be suspicious of any email with a PDF attachment even if it appears to come from someone you know. If it is unusual (e.g. someone sends you an invoice or other document you are not expecting), do not open the attachment.
- If you suspect an email may be a scam, do not reply to that email to verify its authenticity if you have other means of contacting them.
- If you do open the attachment and see a Word or Excel logo prompting you to click on a link to open the document in Office 365
- Do not click on that link
- Notify your IT administrator immediately
- Close the attachment immediately
- Run a full virus scan on your system
- If you do click on the link before you realize it is a scam
- Power down your computer
- Notify your IT administrator immediately